Email Authentication: Using SPF, DMARC & DKIM to Prove Your Emails Are Legit

Ever feel overwhelmed at the volume of spam emails you receive?
If so, you might be surprised to learn that the proportion of mail that ends up in our junk folders has actually dropped significantly in recent years.
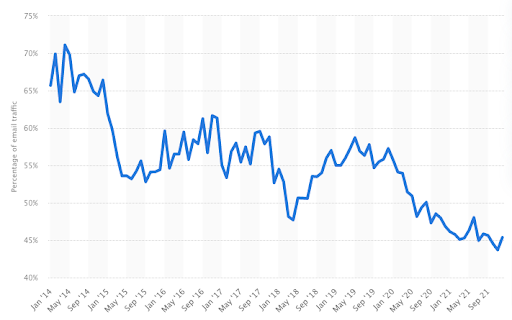
Of course, there’s still a huge amount of junk email out there, with almost half of all emails being classed as spam.
For its part, Google says it blocks more than 100 million phishing emails every single day, with two-thirds of those scam emails never having been seen before.
Clearly, our inboxes are still a dangerous place, so it’s vital that the messages you send are trustworthy. Otherwise, no one’s going to open them.
That’s where email authentication comes in.
In our email authentication guide, we’ll explain what email authentication is and how it works. Along the way, we’ll tell you about the three “pillars” of email authentication:
- Sender Policy Framework (SPF)
- Domain-based Message Authentication, Reporting & Conformance (DMARC)
- DomainKeys Identified Mail (DKIM)
Ready? Then let’s dive in…
What Is Email Authentication?

Imagine you’re queuing up to enter a hot new bar called The Inbox.
You get to the door and the bouncer asks for ID, so you whip out your driving license.
Now, imagine you’re an email, and the doormen are a mailbox provider and a spam filtering system. You wouldn’t show them your license — you’d hand over your email authentication.
That’s a bit of a clumsy metaphor, but hopefully you get the picture: email authentication is effectively a digital ID card that proves an email is legit (in other words, the person or organization named as the sender actually sent it). It’s the set of protocols that prevents harmful or fraudulent emails from reaching our inboxes.
The phrase “set of protocols” is important, because in reality, email authentication isn’t one single “thing”.
It’s actually a bunch of separate — and occasionally overlapping — standards, the most common of which are the aforementioned SPF, DMARC, and DKIM.
Each of those measures was intended to support the Simple Mail Transfer Protocol (better known as SMTP), the system of rules by which email is sent, but which doesn’t actually do anything to verify the sender.
How Does Email Authentication Work?

There’s no single approach to email authentication. Each system has its own technical specification, not to mention its own strengths and weaknesses.
Still, generally speaking, the email authentication process follows these broad steps:
- Company A formulates a policy setting out how to authenticate emails sent from its domain name.
- This policy is published and implemented by configuring the organization’s technical infrastructure, including its mail servers.
- Company B receives an email that appears to be from Company A, so Company B checks if the incoming message complies with the rules laid out in Company A’s email authentication policy.
- Based on the results of this check, Company B will either accept, flag, or reject the email.
In this way, email authentication keeps us safe (or at least safer) from malicious emails, which use a practice known as “email spoofing” to trick us about the origins of the emails we receive.
What Is Email Spoofing?
Email spoofing is a technique by which spammers and phishers try to make it look as if a message they sent was actually sent by a trusted person or organization.
It’s made possible by the fact that outgoing emails servers are unable to identify whether or not the sender address assigned to an email is legitimate or fraudulent.
While these sorts of scams are normally relatively easy to spot, the fact is that most people simply don’t take the time to look out for forged email headers because they receive so many emails.
Instead, they take the fraudulent sender name at face value, which means they trust a message they otherwise wouldn’t.
In turn, that means they’re much more likely to follow through with any requests laid out in the message — such as clicking a hyperlink, sharing a piece of information, or downloading an attachment.
You won’t be surprised to learn that email spoofing attacks are extremely common.
So common, in fact, that Valimail estimates at least one in every 100 emails uses a suspicious — and most likely fraudulent — sender identity.
Or to put it another way, three billion messages a day are sent with a spoofed name in the “From” field.
Scary stuff, right?
Not just because it can leave you vulnerable to phishing attacks, but because your own name — or your organization’s name — could be spoofed and used to send malicious emails to thousands of people.
That can cause major reputational damage.
So it’s reassuring to learn that email domains are almost 5X more likely to be targeted by spoofing attempts if they don’t have DMARC enforcement. In this case, you can use a DMARC checker to ensure your emails are properly authenticated.
Or, to put it another way, if you follow email authentication best practices, your chances of falling victim to email spoofing will be much lower.
The Three Pillars of Email Authentication Explained

Which brings us smoothly to what we like to call the three pillars of email authentication — SPF, DKIM, and DMARC.
In this section, we’ll explain what they are and how they work.
- What Is SPF?
SPF is an email authentication technique based on the Domain Name System (DNS) — the “thing” that turns human-readable domain names (like “Amazon.com”) into machine-readable IP addresses (like “192.0.2.44”).
Essentially, SPF allows you to choose which email servers are allowed to send emails on behalf of your organization.
Every time you send an email address, the receiving server will look for a published SPF record. Provided you’ve set up SPF, that check will result in one of two outcomes:
- Your sending IP address is on the list of valid addresses, so you pass the check. Congratulations!
- Your IP doesn’t appear on the specified list, so the SPF check is failed, and your email will either land in the spam folder or be rejected altogether.
That all sounds pretty watertight, right?
Sadly, it’s never quite as simple as that.
In reality, there are some pretty major limitations to SPF authentication when it comes to validating the source of an email.
Even more concerningly, it doesn’t work at all when a message is forwarded, and it offers no protection in the event that your display name or “Friendly From” address is spoofed.
All of which explains why the second email authentication pillar, DKIM, was introduced in the first place.
Which brings us nicely to…
- What Is DKIM?
DKIM gives each email a digital signature.
Known as a DKIM signature, it’s a secure email header that allows the email recipient to verify that a message was sent and authorized by the owner of the sending domain.
This email authentication technique relies on secure encryption, with part of the secure key available through the public DNS, and the other half kept private. Clever stuff!
Not only does this approach allow the recipient to check that an email was really sent by the apparent sender, but it also flags up if a message was altered in any way during the sending process.
That makes it a whole lot harder to run email spoofing scams.
For this reason, the internal filtering systems used by mailbox providers rely on a combination of SPF and DKIM (alongside a bunch of other algorithmic factors) to protect their users.
But once again, there’s a shortfall here. Neither SPF or DKIM allow domain owners to tell mailbox providers how an email should be treated in the event that an authentication check cannot be validated.
Should the message be placed in the main inbox anyway? Hidden away in the spam folder? Or rejected completely?
That’s why senders also rely on DMARC, which steps in when DKIM or SPF (or both) fail to get the job done…
- What Is DMARC?
DMARC is another email authentication protocol, but as the “R” and “C” in the name suggest, it also incorporates reporting and conformance.
What does that mean in practice?
Well, firstly, DMARC aligns the measures used in DKIM and SPF authentication to verify the authenticity of sent emails, thereby reducing the risk of malicious email. As we noted earlier, non-DMARC-enforced domains are far more susceptible to spoofing attacks.
Beyond that, the protocol also allows domain owners to specify what should be done with messages that fail authentication. They can do this by setting a policy within the DMARC DNS record, with three options to choose from:
- No action: Unauthenticated messages are delivered as normal
- Quarantine: Unauthenticated messages are sent to the spam, junk, or quarantine folder
- Reject: Unauthenticated messages are rejected or bounced back to the sender
The policy element is a vital part of DMARC. It’s not good enough to simply set up DMARC; without an enforcement policy, the receiving server won’t take any special action, even if a message fails authentication. In which case, it was a total waste of time setting up DMARC in the first place.
That might sound obvious to you, but an astonishing number of organizations don’t fully complete the DMARC process.
According to Valimail, just 14.8% of organizational domains have an enforcement policy in place, although some industries — in particular, federal government agencies — perform much better than average.
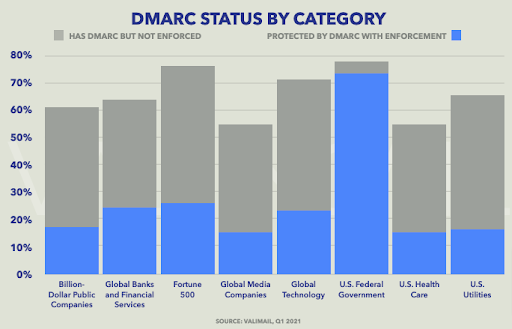
But that’s not all.
Remember the “R” in DMARC?
The reporting element allows domain owners to see where all emails that include their domain in the “From” address were actually sent from.
In other words, it’s a key way to retrospectively identify if your domain is being spoofed to send fraudulent and malicious emails, which means you can take the appropriate steps to stop it happening again.
To Wrap It All Up
It’s easy to dismiss email authentication protocols as nothing more than a bunch of complicated, techy stuff that doesn’t really affect you.
But this is about much more than deciding which emails should land in your junk folder and which should be bounced. It’s about stopping spammers from fraudulently using your name to target people with malicious emails.
That’s a massive deal, because — unfair as it might sound — consumers simply don’t care that you’re the “victim” of a spoofing scam.
They’ll hold you responsible.
Indeed, 61% would lose faith in their favorite brand if they disclosed personal information to a spoofed website or lost money via a phishing scam, according to Mimecast.
So do yourself a favor and set up SPF, DKIM, and DMARC right now!
Free 14-Day Trial
Start building relationships now with your fully-featured 14-day trial!
How We Compare
Terms | Done-For-You Terms | Privacy | Write For Us | Press
© 2024 Postaga. All Rights Reserved. Made with 
